Bevan Briefing #8 - Homeopathic Policy: The Memory of Transformation. What Remains When You Remove All the Evidence
Happy New Year pals. I hope you've entered 2026 rested and recharged. I am still mainly living on leftovers in a student-type way of eating bashed up meals of random ingredients like Ainsley Harriott is watching and judging me and watching too much Murder She Wrote. I hope the liminal space of Betwixtmas was enjoyable and that you are cosy and warm somewhere whilst the blanket of snow envelops the country.
This issue I'm going to be giving my take on the following things which have landed since the last issue:
- The 10 year plan working groups evidence. Dropped just before Christmas and interesting to see what was proposed and left out of the document.
- The UK's cyber action plan which is pan government but clearly has implications for the NHS
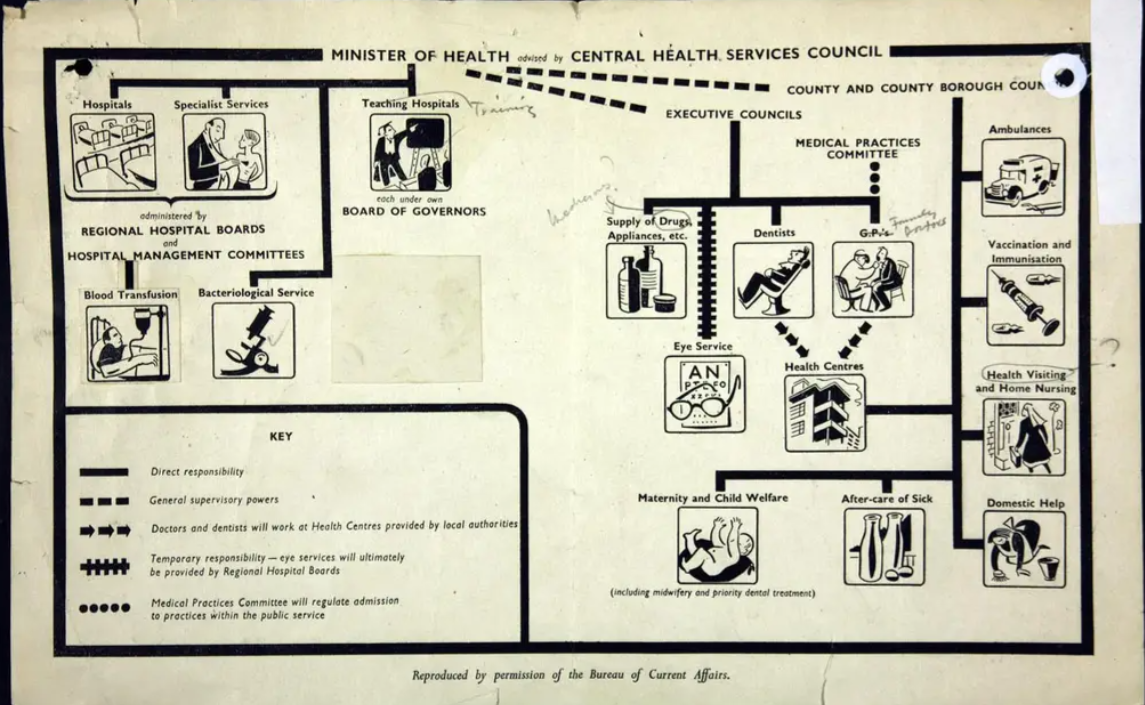
- Re:State's view on patient flow and The Hospital of the Future which forms the basis of the recently announced and much polarising Online Hospital by NHS England.
Let us go cavorting into into the pdfs which are in contravention of the accessibility policy of the same government. Off we go.

What the Working Groups Said (And Government Ignored)
Given the purpose of the working groups is to suggest things for Government, I'm less interested in the stuff that made it through but more interested in the stuff which didn't...
Comparison Table: Working Group Recommendations vs. Final 10-Year Plan
| Theme | Working Group Recommendation | Evidence/Target Cited | Final Plan Commitment | Status |
|---|---|---|---|---|
| PREVENTION & PUBLIC HEALTH | ||||
| Alcohol harm | Minimum unit pricing | Reduces harm, evidence from Scotland | Not mentioned | ❌ MISSING |
| Obesity | Restrict junk food advertising to children | Childhood obesity costs NHS £6.5bn annually | "Restrictions on advertising of less healthy food" mentioned once | ⚠️ VAGUE |
| Tobacco | Smokefree generation - progressive age-of-sale | 75,000 deaths annually, £2.5bn NHS cost | "Create first smokefree generation" mentioned | ⚠️ WEAKENED |
| Prevention ROI | £14 return on every £1 spent | Public Health England evidence | Not used in economic case | ❌ MISSING |
| Health inequalities | Target resources to most deprived areas | 10-year gap in life expectancy | "Address health inequalities" - no funding mechanism | ⚠️ VAGUE |
| NHS anchor institution | Use employment/procurement to improve local economies | £31-33bn annual cost of inequalities | Mentioned once without detail | ❌ MISSING |
| Childhood programs | Expand health visiting, school nursing | Early intervention evidence | Generic mention only | ⚠️ WEAKENED |
| HOSPITAL PRODUCTIVITY | ||||
| Theatre utilization | Improve from 85% to 92% | Would deliver 500,000 extra procedures/year | "Improve productivity" - no target | ❌ TARGET MISSING |
| Length of stay variation | Standardize to reduce waste | £1bn+ annual savings potential | Not specifically addressed | ❌ MISSING |
| Early discharge | 30% more before-midday discharges | Best-performing trust benchmark | Not mentioned | ❌ MISSING |
| Seven-day services | Extend diagnostics & consultant cover across week | Reduces weekend mortality effect | Mentioned but no commitment | ⚠️ VAGUE |
| Surgical hubs | Protected elective centers separate from emergency | 50% lower cancellation rates during pandemic | Mentioned but not as protected model | ⚠️ WEAKENED |
| Demand management | Better use of advice & guidance for referrals | Reduces inappropriate referrals | "Advice and guidance" mentioned | ✅ INCLUDED |
| Clinical pathway standardization | Mandate best practice to eliminate variation | Significant cost savings from reducing variation | "Share best practice" - not mandated | ⚠️ WEAKENED |
| DIGITAL & DATA | ||||
| Single patient record | Unified digital record across all settings by specific date | Estonia/Denmark models show improved coordination | "By end of parliament" - no technical roadmap | ⚠️ VAGUE |
| Open standards mandate | Regulatory requirement for interoperability | Fragmentation costs billions in duplication | "Encourage" open standards - not mandated | ❌ WEAKENED |
| AI deployment targets | AI to save 13-15% of staff time on admin | International evidence of automation potential | "Explore AI potential" - no targets | ❌ MISSING |
| Infrastructure upgrade | Replace outdated systems (Windows 7, pagers) | Security risks and productivity loss | Not mentioned with timeline | ❌ MISSING |
| Patient access to records | Immediate access to test results, appointment booking | Patient satisfaction and engagement | Mentioned but no timeline | ⚠️ VAGUE |
| AI in diagnostics | Deploy AI for imaging, pathology | Evidence from pilot sites | "AI-enabled diagnostics" mentioned | ⚠️ VAGUE |
| Administrative automation | AI for letters, summaries, coding | Frees clinical time | Generic AI mentions only | ⚠️ WEAKENED |
| NEIGHBOURHOOD HEALTH | ||||
| Team structure | Multidisciplinary teams serving 30,000-50,000 populations | Proven integrated care models | "Neighbourhood" undefined - no structure | ❌ MISSING |
| Hospital avoidance | 40% of admissions manageable in community | Evidence from high-performing PCNs | Not quantified | ❌ TARGET MISSING |
| A&E reduction | 15% reduction through integrated care | Rushcliffe PCN evidence | Not mentioned | ❌ MISSING |
| Single point of contact | Guaranteed for complex patients | Improves experience and outcomes | "Better coordination" - no mechanism | ⚠️ VAGUE |
| Social prescribing impact | 30% reduction in GP consultations | Evidence from existing schemes | Mentioned without targets | ⚠️ WEAKENED |
| Proactive care model | Systematic identification of high-risk patients | Prevents escalation | Mentioned but no delivery model | ⚠️ VAGUE |
| Community diagnostics | Expand capacity significantly | Reduces hospital referrals | "Expand community diagnostics" | ✅ INCLUDED |
| Pharmacy First expansion | Extend clinical services in pharmacies | Evidence of safe, effective care | Mentioned positively | ✅ INCLUDED |
| WORKFORCE | ||||
| Growth target | 2% above demographic need annually | Addresses projected shortfall | "Grow workforce" - no specific rate | ❌ TARGET MISSING |
| Medical training | Double medical school places | Long-term pipeline requirement | "More doctors" - not doubling | ⚠️ WEAKENED |
| Agency spend | Reduce £3bn annual agency costs | Waste from poor workforce planning | Not addressed | ❌ MISSING |
| Skill-mix | 70% of junior doctor tasks to PAs/ACPs | Evidence from exemplar sites | "New roles" - no deployment target | ⚠️ WEAKENED |
| Early retention | Address 1-in-10 leaving within first year | Costly turnover and morale impact | Not specifically addressed | ❌ MISSING |
| Flexible working | Guarantee flexible options | Improves retention | "Better working conditions" - generic | ⚠️ VAGUE |
| Anti-bullying | Specific measures to tackle workplace culture | Staff survey shows bullying prevalent | "Improve culture" - no specifics | ⚠️ VAGUE |
| International recruitment | Ethical framework for overseas hiring | Avoids depleting source countries | Not mentioned despite reliance | ❌ MISSING |
| Technology for admin | Use AI to reduce 13% of admin time | Improves job satisfaction | Generic mention only | ⚠️ WEAKENED |
| CROSS-CUTTING | ||||
| Accountability metrics | Specific KPIs for each reform area | Enables tracking and course correction | Limited metrics, "subject to funding" | ❌ WEAKENED |
| Multi-year funding | Certainty for transformation investment | Evidence from previous reforms | "Subject to spending review" throughout | ❌ MISSING |
| Legislative changes | Data sharing, workforce regulation reforms | Legal barriers identified | Barely mentioned | ❌ MISSING |
| Capital investment | Targeted funding for transformation | Infrastructure requirements costed | Not committed | ❌ MISSING |
| Implementation timeline | Phased rollout with milestones | Learning from exemplars | Vague "end of parliament" | ⚠️ VAGUE |
The Most Striking Omission: The Economic Case
The prevention working group's £14 return on every £1 spent is buried. The hospital working group's £1bn from reducing length-of-stay variation isn't used to make the financial case. The workforce working group's £3bn agency spend isn't targeted for reduction.
The plan lost the economic argument that would justify the investment. It's all cost (more staff, more buildings) without the savings case (prevention, productivity, efficiency).
What This Reveals
The 10-year plan is a political document that cherry-picked the popular bits: ✅ More doctors and nurses (everyone wants this) ✅ Digital records (sounds modern) ✅ Care closer to home (poll-tested well)
But stripped out anything requiring hard choices: ❌ Regulating alcohol, tobacco, junk food ❌ Binding productivity targets ❌ Mandating standardization ❌ Specific funding commitments ❌ Legislative reform
The working groups did serious policy work with evidence bases. The final plan took their vibe but left the substance that would enable delivery and accountability.
Digital Transformation on Dial-Up: The NHS's Windows 7 Problem
The Contradiction You're Not Supposed to Notice
In January 2026, the government published its Government Cyber Action Plan acknowledging what NHS staff have known for years: 28% of the government technology estate is legacy and "highly vulnerable to attack." Some NHS trusts are still running Windows 7, an operating system Microsoft stopped supporting in 2020. The government's own assessment? Cyber risk to the public sector is "critically high."
Three months earlier, the NHS Medium Term Planning Framework mandated that by 2028/29, every NHS trust must:
- Make 95% of appointments bookable via the NHS App after triage
- Onboard all acute, community, and mental health providers to the NHS Federated Data Platform
- Migrate all patient communication to NHS Notify
- Deploy ambient voice technology at pace
- Achieve 100% coverage of electronic patient record systems
This is the equivalent of demanding Formula 1 performance from a car held together with duct tape.
The £2-3 Billion Question Nobody Answered
The Cyber Action Plan identifies that fixing the government's infrastructure crisis requires £2-3 billion for "Windows 7 upgrades, WiFi, cloud migration, and cyber security." It describes this investment as "foundational" – a prerequisite for everything else.
But here's what the plan doesn't say: how much of that £2-3 billion is allocated specifically to the NHS.
The Department of Health and Social Care is designated as the Lead Government Department for health sector cyber security, meaning DHSC is accountable for sector-wide cyber resilience. Individual NHS trusts remain responsible for their own cyber security. Yet the Cyber Action Plan, while using NHS incidents as cautionary examples (the Synnovis ransomware attack, the British Library breach), provides no NHS-specific infrastructure funding.
The Medium Term Planning Framework allocates capital spending increasing from £13.6 billion in 2025/26 to £14.6 billion in 2029/30 – a 3.2% average real-terms growth. Sounds generous until you realize that:
- Capital funding covers all infrastructure: buildings, equipment, IT systems, diagnostic machinery
- The NHS has a well-documented maintenance backlog estimated at £11.6 billion in 2023
- The £2-3 billion digital infrastructure need identified by the Cyber Action Plan isn't ring-fenced within this allocation
- The capital approval process remains fundamentally unreformed
The Infrastructure the 10 Year Plan Forgot to Mention
The 10 Year Health Plan working groups did the technical work. Their Digital and Data Working Group specified exactly what infrastructure investment was needed:
- £2-3 billion for Windows 7 replacement, WiFi coverage, cloud migration
- This was identified as mandatory – the foundation on which everything else depends
- Without it, cannot deliver single patient records, AI deployment, or interoperability
The final 10 Year Health Plan published in December 2024? The infrastructure investment commitment disappeared. The plan says the NHS will be "digital by default" with a "single patient record by end of parliament" but is silent on how trusts running Windows 7 will get there.
The working groups were explicit: you cannot build modern digital services on infrastructure that cannot be defended by modern cyber security measures.
The Catch-22 Trusts Actually Face
In practice, NHS trusts face a familiar trap:
To get funding for infrastructure, they must navigate a business case process that, according to Re:State's October 2025 research, is "needlessly lengthy, duplicative, and often inhibits technologies from being readily adopted." Even after the "streamlining" promised in the 10 Year Health Plan, capital approval takes a minimum of 2-4 months for smaller schemes, longer for major investments. There's often a lag between approval and funds arriving as lots of FDs who are part of the Frontline Digitisation programme will tell you.
The turnaround time matters because trusts are simultaneously mandated to deliver 2% annual productivity improvement (locked into the Spending Review settlement) while meeting ambitious digital transformation targets. Every month spent waiting for capital approval is a month without the tools to deliver the productivity gains that would help pay for those tools.
The perverse incentive: Re:State found that trusts with access to charitable funds often choose to fund innovation through their charity rather than the capital approval process "because it is quicker and easier to obtain the funds." This means digital transformation is faster for trusts lucky enough to have generous donors – embedding postcode lottery into infrastructure investment.
The Foundation Trust privilege: Under the reformed capital regime, Foundation Trusts (154 of 229 trusts) get more autonomy to determine capital spend. Non-Foundation Trusts still go through centralized approval. But Foundation Trust status is granted based on financial sustainability and governance quality – the very things that are harder to achieve without infrastructure investment. It's a circular trap.
The Technology Works. The System Blocks It.
The frustrating reality is that the technology to solve many NHS operational problems already exists and has been successfully deployed:
Maidstone and Tunbridge Wells NHS Trust deployed a centralized patient tracking solution in 2020. It halved bed turnaround time, gives real-time visibility of 740 beds and 4,000+ patient transfers monthly, and reduced time to transfer patients from ED to inpatient bed by 26% in the first three months. The technology works. It's now being scaled to community hospitals.
Kettering General Hospital used AI to improve bed scheduling, creating a digital twin hospital using five years of historic data. This gave them ability to forecast demand and test scenarios. The code is openly available on GitHub. Anyone could deploy it tomorrow.
Gloucestershire Hospitals NHS Foundation Trust deployed AI to predict "long-stayers" (patients staying 21+ days, who comprise 4% of admissions but 34% of bed days). The model detected 66% of long-stayers within highest risk categories. A single-day reduction in average stay yields £1.7 million in savings for this trust alone. The proof of concept is complete, integrated with the electronic health record via APIs, and tested against real data.
The barrier isn't the technology. It's the business case process, the capital approval delays, and the absence of dedicated change management capacity to implement and embed new ways of working.
The Management Problem Nobody Mentions
Here's an uncomfortable reality: the NHS doesn't just have an infrastructure problem. It has a management problem. And you can't implement digital transformation without operational managers to make it work.
Re:State's November 2025 synthesis found that the NHS is "woefully undermanaged": managers make up only 1.9% of the NHS workforce, compared to 11% in the wider economy. The UK spends 2p in the pound on healthcare administration compared to 5p in Germany and 6p in France.
This matters because managers aren't a homogeneous class of bureaucrats. They're the people who:
- Ensure A&E and diagnostics run smoothly day-to-day (operational managers)
- Coordinate staff, finance, and performance across entire hospitals with budgets exceeding £1 billion (senior managers)
- Ensure processes and workflows are adapted when new innovations are introduced (change managers)
That last category is critical. Re:State interviewed multiple NHS leaders who emphasized that "change management as a formal function is rarely prioritised in hospitals" and is "a different skill set to that of most staff." Many NHS transformation roles are fixed-term positions tied to temporary programmes or external funding, making them "fragile and temporary."
You cannot deploy Teletracking, implement digital twins, or roll out AI prediction models without change managers to redesign workflows, train staff, and embed new ways of working. The Medium Term Planning Framework mandates comprehensive digital transformation without addressing the change management capacity deficit that prevents trusts from implementing that transformation.
This is why the Innovator Passport promise matters but only if it includes already-deployed technologies. The proposal doesn't clarify whether it applies retrospectively. There's a risk of significant backlog: innovations with years of evidence waiting for passport status while being treated as "not yet approved" elsewhere.
The Mandates Without the Means
The Medium Term Planning Framework mandates that by end of 2028/29:
- Digital Capabilities Framework: 100% compliance with minimum standards, including universal EPR coverage "as soon as possible"
- Core National Products: 100% implementation by end 2027/28, including Electronic Prescription Service, Electronic Referral Service APIs, consolidation of NHS.Net Connect, integration of all existing NHS App capabilities
- NHS Federated Data Platform: All acute, community, mental health providers onboarded and using core products for elective recovery, cancer, UEC. ICBs must use population health management tools from FDP for strategic commissioning.
- NHS App: 95% of appointments bookable via NHS App after triage across all care settings. Full coverage of patient medicine management, waiting times, pre/post-appointment questionnaires, digital PIFU.
- NHS Notify: All direct-to-patient communication migrated, terminating local arrangements. NHS App "push" notifications as preferred contact method.
These aren't suggestions. They're requirements. Trusts must demonstrate in their 5-year plans how they will deliver them.
But the Framework is silent on:
- How trusts running legacy infrastructure will implement these systems
- What happens to trusts that cannot afford the infrastructure investment required
- How the business case process will be expedited for mandated technologies
- Whether the £2-3bn infrastructure investment identified by the Cyber Action Plan is allocated within the capital envelope
- How trusts will acquire the change management capacity to implement these transformations
The Framework does promise "updated guidance on new delegated limits" for capital and business case templates available through regional teams. But delegation without adequate capital allocation is meaningless. Streamlining the approval process for investments you cannot afford doesn't solve the problem.

Why Technology Alone Won't Save You
Re:State's synthesis makes a crucial point that policymakers consistently miss: "Technology will only help insofar that the entire system is reformed alongside it."
The NHS is not a monolith that can be bent to government's will through central mandates. It's a complex web of relatively autonomous institutions, funded by a patchwork of financial incentives, with a highly specialised workforce that comes with its own well-established processes and ways of working.
Financial incentives sit at the heart of the system. As Re:State notes, "what maintains the current model of hospital care are entrenched financial flows, outdated care pathways, and workforce culture and incentives. No matter how revolutionary the technology, so long as these ossified structures stay in place, the hospital will continue to dominate."
You can mandate that 95% of appointments are bookable via NHS App, but if GPs are still paid per registered patient rather than per consultation, the financial incentive to shift consultations to the app is weak. You can mandate NHS Federated Data Platform adoption, but if trusts aren't funded for the quality improvements that data enables (only for treating more patients), they have no financial incentive to use it effectively. Equally the funding needs to help those with legacy to modernise to engage with the programme - it doesn't work on Windows 7.
Care pathways – the protocols for treating particular conditions – have seldom been adapted for modern clinical realities. These processes underpin all cross-organisation interaction in the NHS. Re:State found that reforming them would be "an essential precondition for a more integrated hospital of the future." It's not clear this has taken place, particularly for multimorbidity pathways which dominate healthcare use and expenditure. Particularly those which cross mental and physical health.
Workforce structures were built around episodic, hospital-based care. Doctors are trained in narrow clinical specialisms when the system desperately needs expert generalists. Without redesigning roles and career structures, the system will continue to pull activity back toward hospitals, regardless of technological innovation.
The Medium Term Planning Framework mandates digital transformation without addressing any of these fundamental structural barriers. It assumes technology can be overlaid on an unchanged system and produce transformation. This is magical thinking.
When Targets Replace Strategy
The 2022 Government Cyber Security Strategy set a target: all government organisations to be "resilient to known vulnerabilities and attack methods" by 2030.
The January 2026 Cyber Action Plan officially abandoned this target as "not achievable by the original target date" due to:
- Institutionalized fragmentation
- Persistent legacy and cyber security risks
- Under-digitization
- Inconsistent leadership
- Digital skills shortfall
- Outdated funding models
These aren't technical problems. They're system design problems. And they're the same problems undermining digital transformation in the NHS.
The new Cyber Action Plan extends the timeline: "Building" phase by March 2027, "Scaling" phase by April 2029, "Improving" phase from April 2029 onwards. This means the government now expects to achieve in 2029+ what it originally thought achievable by 2030, despite having spent four years moving backwards.
Meanwhile, the NHS is mandated to achieve comprehensive digital transformation by end of 2028/29 on infrastructure the Cyber Action Plan describes as critically vulnerable.
The Productivity Paradox Nobody Mentions
The Medium Term Planning Framework locks in 2% annual productivity improvement as a requirement, not an aspiration. This is the foundation of the financial settlement. Without it, the numbers don't work.
But mandating productivity improvement while maintaining the structural barriers to that improvement is magical thinking.
Re:State's analysis of patient flow demonstrates that productivity in acute hospitals has been declining despite significant increases in staff:
- HCHS doctors continuously increased at much faster rate than demand
- Secondary care nurses and health visitors similar pattern
- Yet productivity grew 2.7% in 2024/25 after years of decline, still below pre-COVID levels
- Since 2019/20, NHS workforce has grown much faster than activity
The productivity problem isn't lack of staff. It's how those staff are deployed and the tools they have available.
Here's why digital tools can help in healthcare when historically they couldn't: Re:State's synthesis identifies that "there is a structural limit on labour productivity gains because so much of the 'output' is direct professional care time." A nurse cannot safely halve the time they spend with each patient. A surgeon can't perform twice as many operations per day without risk.
By contrast, in manufacturing, machines and automation can dramatically increase output per worker. This is why healthcare productivity has historically lagged behind other sectors.
But technology subverts this limitation: Remote secondary care reduces labour input while simultaneously increasing supply of services. Virtual wards require less staff to observe more patients compared to inpatient wards. Remote monitoring enables complex patients to be monitored with almost no human intervention unless observations indicate a problem.
Digital tools can help but only if:
- The infrastructure exists to run them (it doesn't for 28% of the estate)
- The capital approval process allows rapid deployment (it doesn't – 2-4 months minimum, more like 12 months in my experience)
- Change management capacity exists to implement and embed (Re:State found it "inconsistently applied and generally insufficient")
- The operational barriers are addressed (weekend working, over-specialization, management capacity)
- Financial incentives reward the productivity gains rather than just more activity
- Care pathways are redesigned to exploit the new capabilities
- Workforce roles are adapted to work differently
Technology is necessary but not sufficient. The Framework mandates the technology without addressing the sufficient conditions.
The Government Cyber Unit will publish trust-level productivity statistics monthly as official statistics. This transparency is valuable. But publishing data that shows trusts failing to meet mandated targets because they lack the infrastructure investment, change management capacity, and system reforms to deliver those targets is accountability theatre, not accountability.
The Hidden Cost of Doing This Properly
Re:State's synthesis includes an uncomfortable truth about reform costs that policymakers need to hear: "Policymakers and NHS leaders should not embark on radical hospital reform expecting immediate, direct financial savings."
The evidence from US healthcare is instructive. In 1984, $3 billion was spent treating heart attacks. By 1998, this rose to $4.8 billion despite heart attacks declining 1% annually due to prevention. Why? Because the methods to treat them became more expensive and were used by more people.
Innovation increased direct healthcare costs. But analysis suggests for every $1 extra spent on heart attacks, the gain to society was $7 – through longer, healthier, more productive lives.
Re:State warns: "With previous waves of innovation, greater efficiency often enables more activity – more patients seen and treated – which increases overall spending, but this increases slower than it otherwise would have done due to productivity increases."
This applies directly to digital transformation:
Virtual wards enable trusts to see more patients with less staff input per patient. Sounds like it should cut costs. But Re:State cautions that without careful management, virtual wards risk being "additive to a service, rather than a replacement." If physical wards aren't actually closed when virtual capacity opens up, you've just expanded total capacity. Overall service usage increases. Costs don't fall – they rise more slowly than they would have.
Community Diagnostic Centres were meant to reduce hospital waiting times by creating additional capacity in the community. Re:State found they often face "supply-induced demand" – build more capacity, and more people use it, even when they might not have needed to. "The degree of unmet demand in the health system means additional capacity is often quickly consumed, and costs rise while waiting times stagnate."
The NHS App will make appointments more accessible. But more accessible appointments may mean more appointments booked, not just shorter waits for the same number of appointments. If GPs aren't funded to handle the increased volume, you've created a tool that makes it easier to access a service that doesn't have capacity to deliver.
None of this means these innovations are bad. It means reform needs to be designed with realistic cost expectations. The value lies not in immediate savings but in better use of constrained resources: shorter waiting lists, improved access to care, more sustainable workloads for staff. There needs to be a proper review of unmet demand to understand how much expansion is likely to take place.
Creating the hospital of the future will require significant investment. Expanding change management capacity, introducing new technologies, testing alternative payment models, redesigning care pathways, reforming workforce training – all cost money upfront.
The cost of not investing is far higher. Opportunity cost is particularly acute in health policy. Inaction means rising demand meets static capacity, worsening outcomes, increasing inefficiency. The Medium Term Planning Framework's 2% productivity requirement becomes unachievable. Performance targets continue to be missed. Patient harm accelerates.
The Choice Nobody Wants to Make
The government needs to make a choice it's been avoiding:
Option 1: Properly fund NHS infrastructure investment
- Ring-fence the £2-3bn identified by Cyber Action Plan specifically for NHS digital infrastructure
- Make this additional to, not part of, existing capital allocations already committed to buildings, equipment, diagnostics
- Front-load investment to enable digital transformation rather than expecting transformation to somehow happen first
- Fund the change management capacity needed to implement these systems
- Accept that this will increase costs in short term but slow cost acceleration over time
Option 2: Extend the digital transformation timeline
- Acknowledge that mandating 2028/29 delivery on critically vulnerable infrastructure is unrealistic
- Align NHS digital transformation timeline with Cyber Action Plan phases (completion April 2029+)
- Stop pretending you can build 21st century services on 20th century foundations
- Give trusts time to build change management capacity and redesign pathways
- Accept that structural system reforms (funding models, workforce training, care pathways) need to happen alongside technology deployment
Option 3: Reform the system, not just the technology
- Address the financial incentives that keep resources flowing into hospitals
- Redesign care pathways for modern clinical realities, particularly multimorbidity
- Reform workforce training to create expert generalists, not just narrow specialists
- Expand and professionalize operational and change management
- Devolve real financial autonomy to Integrated Care Systems to design local incentives
- Accept that technology is necessary but not sufficient for transformation
Option 4: Admit the 10 Year Health Plan timeline is undeliverable as written
- The working groups were right: infrastructure investment is prerequisite
- The final plan removed that inconvenient truth
- The Medium Term Planning Framework mandates delivery anyway
- One of these documents is wrong
The government appears to be trying to have it all: ambitious digital transformation mandates, 2% productivity requirements, but without the infrastructure investment, system reforms, change management capacity, or timeline adjustment needed to make either achievable.
What we have instead is strategic incoherence: the Cyber Action Plan says the infrastructure is critically vulnerable, the Medium Term Planning Framework mandates comprehensive digital transformation on that infrastructure, the 10 Year Health Plan removed the costed infrastructure investment the working groups said was foundational, and nobody has addressed the financial incentives, care pathways, workforce structures, or management deficit that prevent digital transformation from working even when the infrastructure exists.
Meanwhile NHS trusts are expected to navigate a business case process that takes months, operate on capital budgets that must cover buildings and equipment as well as IT, deliver monthly productivity statistics showing progress on mandates they lack the infrastructure to meet, implement transformations they don't have change managers to embed, and work within financial incentives that reward activity rather than efficiency.
This isn't a plan. It's performance art.

When Cyber Risk Becomes Patient Risk: The Synnovis Attack Nobody Connected to Flow
The Attack That Was Really a Flow Crisis
On 3 June 2024, Synnovis – a pathology partnership serving six NHS trusts across south-east London – was hit by ransomware. Blood testing stopped. Surgery was cancelled. The impact cascaded across Guy's and St Thomas', King's College Hospital, Royal Brompton, Evelina London Children's Hospital, and primary care services across the region.
The immediate headlines focused on cyber security: another NHS ransomware attack, data stolen by the Qilin gang, investigations by the National Crime Agency and NCSC. The attack was analyzed as a security failure.
But walk through what actually happened to patients, and you see something else: the Synnovis attack was a patient flow catastrophe where cyber security failure was the root cause, not the defining feature.
When pathology testing stopped:
- Elective surgery was cancelled (can't operate without pre-op blood work or ability to cross-match blood)
- Emergency department congestion increased (patients requiring blood tests stuck in ED)
- Inpatient discharge delayed (can't discharge patients requiring blood results to confirm safety)
- Diagnostic pathways broke (cancer patients, urgent referrals, all pathways requiring pathology input)
- Ambulance handovers delayed (knock-on effect from ED congestion)
- Primary care referrals disrupted (GPs unable to refer patients requiring pathology investigations)
This wasn't one trust having an IT problem. This was a system-wide operational flow failure affecting hundreds of thousands of patients, triggered by a cyber incident at a single critical supplier.
Yet when government published three major policy documents between October 2025 and January 2026 – the NHS Medium Term Planning Framework, the Government Cyber Action Plan, and Re:State's analysis of hospital patient flow – none of them connected cyber resilience to operational resilience.
The Cyber Action Plan mentions Synnovis as evidence of cyber risk requiring urgent action. Re:State's patient flow analysis examines bottlenecks, discharge delays, operational inefficiency – without mentioning cyber security. The Medium Term Planning Framework mandates digital transformation while requiring cyber security compliance, treating them as separate workstreams.
This siloed thinking is the problem.
The Flow Crisis Everyone Can See
Re:State's October 2025 report "Ending the Patient Gridlock" provides compelling evidence that patient flow is the fundamental productivity crisis in NHS hospitals.
The numbers are stark:
- 268 excess deaths per week in 2023 associated with patients waiting 12+ hours in A&E
- 13,740 patients stuck in hospital despite being medically fit for discharge (February 2025) – equivalent to 23 hospitals' worth of capacity
- £1.7 billion annual direct costs from delayed discharge
- 90% of nurses reported patient safety compromised by corridor care (January 2025)
Re:State demonstrates this isn't a capacity problem – demand for emergency hospital care has grown slowly while clinical staff increased substantially. Input is increasing while output is decreasing. This is a flow problem.
But here's what Re:State's analysis misses: Every cyber incident is a flow incident.
When Synnovis was attacked:
- Blood test capacity dropped to zero overnight
- Elective surgery (flow through planned care pathways) stopped
- ED congestion (emergency flow) increased
- Discharge (flow out of hospital) delayed
- Diagnostic pathways (flow through investigation) broke
The operational problems Re:State analyzes – bottlenecks in diagnostics, discharge delays, ED congestion, cancelled elective procedures – are exactly what happens during a cyber incident, except the trigger is malicious rather than operational dysfunction.
Understanding Hospitals as Systems (Not Collections of Departments)
Before we can understand why cyber and operational resilience are connected, we need to understand how hospitals actually work. Re:State's November 2025 synthesis makes a crucial point: "The hospital is too often defined by its individual functions, for example Accident and Emergency or surgery, but rarely how these functions interact with each other."
This matters because hospitals have multiple interdependencies and can work in non-linear ways. Interventions in one area can have unintended consequences elsewhere. Reducing surgery waiting times might overload recovery wards or cause bottlenecks in community care if follow-up support isn't ready.
Re:State suggests hospitals should be understood more like factories – both have:
- Standardized processes to ensure consistency and efficiency
- Specialization of labour in different parts of the clinical pathway (like an assembly line)
- Highly targeted resource and capacity management between departments
- Consistent quality control throughout the patient journey
The comparison isn't dehumanising – it's about recognizing that standardizing the right processes improves both efficiency and personal experience of care.
Surgical hubs demonstrate this perfectly. By deliberately separating emergency versus planned surgical pathways, they allow the planned pathway to "operate on a low-variation basis" with "high efficiency and predictable throughput." Their success in increasing elective activity versus traditional hospitals clearly demonstrates the value of systems thinking.
This is why cyber incidents cascade so catastrophically through hospitals: Because hospitals are tightly-coupled systems where failure in one component amplifies through the whole. When pathology testing stops, it doesn't just affect pathology – it affects every pathway that depends on blood tests. Which is most of them.
Four Vulnerabilities. Same Root Causes.
Both patient flow failure and cyber security failure stem from the same systemic weaknesses:
1. Infrastructure That's Too Old to Work and Too Old to Secure
Re:State identifies: Hospitals use "midnight census" (counting occupied beds at 11:59pm) rather than real-time tracking. Manual processes – phone calls to wards, physically attending wards, writing down bed availability. This is "time-consuming" and means "planning by averages."
Cyber Action Plan identifies: 28% of government technology estate is legacy, "highly vulnerable to attack," cannot be defended by modern cyber security measures. Some NHS trusts still running Windows 7 (Microsoft ended support in 2020).
The connection: You cannot implement real-time patient tracking tools on infrastructure running Windows 7. The operational inefficiency Re:State identifies and the cyber vulnerability the Cyber Action Plan identifies are two faces of the same problem: infrastructure that's too old to be either efficient or secure.
2. Single Points of Failure (Efficient Until They're Not)
Synnovis demonstrated: A single pathology provider serving six trusts across south-east London. When it failed, regional patient flow collapsed. This is a concentration risk – efficiency through consolidation creating catastrophic single points of failure.
Re:State identifies similar concentration risks in flow:
- Discharge coordinators, pharmacists, occupational therapists, care package assessors often work Monday-Friday only. When they're unavailable (weekends), discharge drops 39-40%. This creates artificial Monday surge.
- Specialist consultants as bottlenecks: patients with multiple conditions need input from respiratory, endocrinology, geriatrics – but no single clinician "owns" the discharge decision on a general ward.
- Diagnostic services: patients waiting for scans, blood tests, pathology results. When these bottleneck, entire pathways stop.
The pattern: Critical functions with insufficient redundancy. Whether the trigger is cyber attack, weekend staffing, or over-specialization, the result is the same – flow stops.
Why this happens: Re:State's synthesis explains that concentration looks like efficiency in normal operations. Consolidating pathology services reduces duplication, saves money, improves utilization. Specialist consultants provide expert care in their domains. Monday-Friday discharge workforce reduces weekend staffing costs.
But optimization that makes normal operations efficient makes disruption catastrophic. The same efficiency gains that reduce cost in steady state amplify system fragility when anything goes wrong. Things can be both strong and brittle.
3. Tight Integration Without Resilience
The 2024 CrowdStrike outage demonstrated this perfectly. Not a cyber attack – a faulty software update. But the Cyber Action Plan notes it "cost the UK economy between £1.7 and £2.3 billion" and "exposed vulnerabilities similar to those seen in malicious incidents."
The problem: Single supplier dependency creating widespread disruption. The vulnerability: Systems so tightly integrated that failure in one component cascades everywhere.
Re:State identifies the same problem in patient flow:
- Hospitals have "multiple interdependencies and can work in non-linear ways"
- "Optimising one service area does not automatically result in performance improvements across the wider hospital"
- "Interventions in one area can have unintended consequences elsewhere"
- Example: Reducing surgery waiting times might overload recovery wards or cause bottlenecks in community care if follow-up support isn't ready
The vulnerability: Interdependence without resilience. Whether the disruption is cyber attack, operational bottleneck, or staff absence, tightly-coupled systems without redundancy amplify rather than absorb shock.
This is the factory analogy Re:State uses: in a well-designed factory, components flow smoothly from one stage to the next with minimal buffering. This maximizes efficiency. But it also means any disruption to one stage immediately affects all downstream stages. Just-in-time manufacturing is extraordinarily efficient until supply chains break. Just ask JLR.
Hospitals operate similarly. Patients flow from ED to assessment to diagnostics to specialist review to ward to discharge. Each stage depends on the previous one. When diagnostics fail (whether from cyber attack or operational bottleneck), the entire flow breaks.
4. Flying Blind in Both Directions
Cyber Action Plan commitment: Government organizations should have "timely access to relevant and actionable cyber security and resilience data that enhances their ability to make effective risk management decisions."
Currently they don't. The Cyber Action Plan found that risk owners lack "visibility and understanding of cyber risk and resilience levels within their purview, and the actual and potential impact on business delivery and critical services."
Re:State identifies identical problem for operational flow:
- Current metrics are "point in time" measurements rather than continuous data
- Midnight census is "outdated" – doesn't capture intraday fluctuations from day patients
- Bed allocation scheduling "managed by a human team who rely on individual expertise, similar to air traffic control"
- "The most common approach across many NHS departments remains a reliance on spreadsheets"
The parallel: Without real-time visibility, you cannot manage risk proactively – whether that risk is cyber attack or operational bottleneck. You're flying blind, reacting to problems rather than preventing them.
Re:State's synthesis emphasizes this: "Optimising patient flow is a basic prerequisite for an NHS facing relentless growth in both the volume and complexity of demand." But you can't optimize what you can't measure. And you can't measure effectively when you're counting beds at midnight and tracking patients on spreadsheets.
The Cost of Pretending These Are Separate Problems
Treating cyber resilience and operational resilience as separate domains has real costs.
NHS trusts don't include cyber disruption in flow planning
Re:State interviewed 11 NHS leaders about patient flow. Not one mentioned cyber resilience as a flow risk. The Framework for patient flow optimization focuses on:
- Workforce deployment (weekend working, consultant coverage)
- Bed management (real-time tracking tools)
- Discharge processes (multidisciplinary coordination)
- Management capacity (operational leadership)
But doesn't include:
- What happens to flow when EPR system goes down?
- How does pathology failure cascade through flow?
- What's the recovery time objective for critical flow-enabling systems?
- Who owns the decision to continue operating during degraded IT capability?
This means recovery plans don't account for what actually happens during cyber incidents – the operational flow failures that harm patients.
Cyber Action Plan doesn't account for operational dependencies
The Cyber Action Plan requires NHS trusts to:
- Implement Cyber Assessment Framework outcomes
- Deploy protective monitoring
- Establish incident response plans
- Report cyber risks to DHSC as Lead Government Department
But the Framework assesses cyber security controls, not operational resilience during cyber incidents.
For example, the Cyber Assessment Framework would assess whether a trust has:
- Asset management (knowing what systems exist)
- Vulnerability management (patching systems)
- Protective monitoring (detecting threats)
- Incident response planning (documented procedures)
It does NOT assess:
- Can elective surgery continue if pathology fails?
- What's the workaround if bed management system crashes?
- How long can ED operate without EPR access?
- Who decides which patients get prioritized during degraded capability?
This means cyber resilience planning optimizes for IT recovery time, not clinical care continuity.
The Medium Term Planning Framework mandates both without connecting them
The Framework requires trusts to:
- Deliver 2% annual productivity improvement
- Meet ambitious operational targets (92% elective within 18 weeks, 85% A&E within 4 hours)
- Implement comprehensive digital transformation (NHS App, NHS Federated Data Platform, NHS Notify)
- Comply with cyber security requirements
But treats these as separate workstreams. There's no requirement to model: What happens to operational targets during cyber incident?
If a trust is mandating 95% of appointments bookable via NHS App by 2028/29, what's the operational fallback when NHS App is compromised?
If a trust is required to migrate all patient communication to NHS Notify (terminating local arrangements), what happens when NHS Notify experiences an outage?
If a trust onboards to NHS Federated Data Platform for performance management, how do they manage performance during FDP disruption?
The Framework mandates digital dependency without requiring resilience planning for that dependency.
The management problem undermines both
As discussed in the infrastructure analysis, the NHS is woefully undermanaged (managers comprise only 1.9% of workforce versus 11% in wider economy). This management deficit directly undermines resilience planning:
Operational managers ensure services run smoothly day-to-day. Without sufficient capacity, hospitals struggle to maintain baseline patient flow. Re:State found "the most common approach across many NHS departments remains a reliance on spreadsheets" for bed management – not because sophisticated tools don't exist, but because trusts lack the operational management capacity to implement them.
Change managers ensure processes adapt when innovations are introduced. Re:State found "change management as a formal function is rarely prioritised in hospitals." When trusts try to implement new patient flow technologies, they lack the change management capacity to redesign workflows and embed new ways of working.
Senior managers coordinate entire hospitals. They're responsible for integrating cyber resilience planning with operational flow planning. But with management stretched thin, these strategic connections don't get made.
The result: Cyber planning happens in IT departments. Operational flow planning happens in clinical departments. Nobody has the management capacity to connect them.
What Synnovis Actually Taught Us (If Anyone Was Listening)
The Synnovis attack provided a near-perfect natural experiment. A single critical service failed. We got to observe exactly how cyber disruption cascades into operational flow failure, affecting patient care across multiple trusts, multiple care settings, hundreds of thousands of patients.
What we should have learned:
1. Cyber incidents are operational incidents (with extra steps)
Synnovis wasn't just a data breach or ransomware attack. It was:
- An elective care crisis (cancelled surgeries)
- An emergency care crisis (ED congestion from inability to test/treat)
- A discharge crisis (patients stuck without confirmatory blood work)
- A diagnostic pathway crisis (cancer patients, urgent referrals delayed)
- A primary care crisis (GPs unable to refer patients requiring investigations)
When government analyzes cyber incidents as security failures rather than operational failures, they optimize for the wrong outcomes. The Cyber Action Plan focuses on preventing breaches, detecting threats, recovering IT systems. It should focus on maintaining patient care during IT disruption.
2. Concentration risk looks like efficiency until it catastrophically fails
Synnovis served six trusts across south-east London – efficiency through consolidation. When it failed, the entire region's pathology capacity failed simultaneously. No redundancy. No failover. Complete operational halt.
This is precisely analogous to the flow bottlenecks Re:State identifies:
- Discharge workforce working Monday-Friday only: efficient staffing, but weekend discharge drops 39-40%
- Specialist consultants as bottlenecks: efficient specialism, but patients with multiple conditions stuck waiting for multiple specialists
- Diagnostic services as chokepoints: efficient centralization, but any disruption stops all pathways requiring that diagnostic
Re:State's synthesis makes the mechanism clear: "Interventions in one area can have unintended consequences elsewhere." Consolidating pathology to achieve economies of scale seemed efficient. Until the consolidated provider failed and took down regional patient care.
NHS needs to map: Where are the single points of failure in patient flow? Include both operational bottlenecks (Re:State's analysis) AND technology dependencies (Cyber Action Plan's concern). Then build redundancy into both.
3. Recovery time objectives need to reflect clinical reality, not IT convenience
Typical cyber incident response plan focuses on IT recovery time:
- How quickly can we restore EPR system?
- How quickly can we recover pathology connectivity?
- How quickly can we bring systems back online?
But the relevant question for patient care is: How long can clinical operations maintain acceptable safety without these systems?
ED can probably operate safely for a few hours without EPR if staff switch to paper records. But not 24 hours. Not multiple days. At some point, patient safety is compromised.
Elective surgery can probably be delayed 24-48 hours safely. But not weeks. Patients on cancer pathways have urgent clinical need.
The recovery time objective should be determined by clinical safety requirements, not IT convenience.
Yet Re:State found that operational planning and cyber planning are siloed. Operational managers plan flow assuming IT systems work. IT plans cyber recovery assuming clinical operations can pause. Neither assumption holds during real incidents.
Re:State's synthesis emphasizes: "It is crucial to consider how all sub-systems in the hospital interact, and in turn take into account the whole unit." This systems thinking needs to extend to cyber planning. Can't plan IT recovery in isolation from clinical operations.
4. Third-party risk is patient risk (whether the contract says so or not)
Synnovis wasn't an NHS trust. It was a pathology partnership – a supplier. But when it failed, patient care across six NHS trusts failed.
The Cyber Action Plan addresses this obliquely: government organizations are "responsible for applying appropriate mechanisms (including good procurement practices, contractual security and resilience terms and audit and review processes) to ensure that supply chain organisations understand their accountability and responsibility for government cyber security and resilience."
But this is insufficient. Contractual terms don't prevent ransomware attacks. Audit processes don't restore pathology testing capacity.
NHS needs to map: Which third-party services are critical to patient flow? For each, what's the operational impact of failure? What's the redundancy? What's the recovery time?
This isn't in the Cyber Action Plan. It's not in Re:State's patient flow analysis. It's not in the Medium Term Planning Framework. Nobody owns the intersection.
The British Library Problem (Still Ongoing 20 Months Later)
The Cyber Action Plan uses the 2023 British Library ransomware attack as a cautionary example. The attack revealed "serious weaknesses due to underinvestment in technology and cyber defences. Recovery is ongoing and the Library is now planning major upgrades."
Recovery is ongoing. Twenty months after the attack, the British Library was still recovering. Not IT recovery – that took weeks. Operational recovery. Restoring services. Rebuilding capability.
Now imagine that timeline for an NHS trust.
A major hospital hit by ransomware attack. IT systems restored in weeks (optimistically). But operational recovery? How long to clear the backlog of cancelled elective procedures? How long to restore diagnostic pathway flow? How long to recover the discharge delays that cascaded during the incident?
Cyber incidents create operational debt that takes months to clear, even after IT systems are restored.
Re:State found that in February 2025, 13,740 patients were stuck in hospital despite being medically fit for discharge. This is steady-state operational dysfunction. Now add a cyber incident on top. How long to recover?
The Medium Term Planning Framework mandates that trusts deliver:
- 92% elective within 18 weeks by 2028/29
- 85% A&E within 4 hours average for the year
- 2% annual productivity improvement
These targets assume continuous operational capability. A single major cyber incident could set a trust back months on these targets. But the Framework has no provision for "operational debt recovery" following cyber disruption.
What Should Actually Happen (Five Things Government Won't Do)
Government needs to stop treating cyber resilience and operational resilience as separate domains. Here's how:
1. Integrate cyber disruption into patient flow modeling
Re:State recommends that trusts deploy:
- Digital twins for simulation (testing "what-if" scenarios)
- AI demand and flow prediction
- Real-time teletracking tools
These tools should model cyber disruption scenarios:
- What happens to elective flow if EPR system down for 48 hours?
- How does pathology failure cascade through diagnostic pathways?
- Can ED maintain patient safety without bed management system? For how long?
- What's the discharge backlog after 72-hour incident?
This would reveal which IT systems are genuinely critical to patient flow (versus merely convenient), inform recovery time objectives based on clinical need, and identify where operational workarounds need to be pre-planned.
Re:State's synthesis emphasizes hospitals as systems with interdependencies. Cyber disruption modeling should follow that systems thinking: trace how IT failure cascades through clinical pathways, not just how quickly IT can be restored.
2. Redefine cyber incident response around operational continuity
Current incident response plans follow IT recovery logic:
- Detect threat
- Contain spread
- Eradicate threat
- Recover systems
- Learn lessons
This should be inverted to clinical safety logic:
- Maintain patient safety
- Prioritize flow through critical pathways (ED, critical care, maternity)
- Deprioritize flow through deferrable pathways (routine elective, non-urgent diagnostics)
- Restore IT systems to support clinical priorities
- Clear operational backlog
- Learn operational resilience lessons (not just cyber security lessons)
The difference: IT recovery becomes the means to operational continuity, not the end in itself.
This aligns with Re:State's finding that hospitals should be understood as systems where "optimising one service area does not automatically result in performance improvements across the wider hospital." Can't optimize IT recovery without considering operational dependencies.
3. Mandate operational resilience testing, not just cyber security testing
The Cyber Action Plan requires government organizations to conduct "exercising and continually improving robust plans at every level, covering likely and high-risk scenarios."
Typically this means tabletop exercises: if ransomware hits, who do we call? How do we contain it? When do we restore from backup?
This should include operational resilience testing:
- Run an elective surgery day without EPR access (paper records only)
- Simulate pathology failure for 48 hours (how do clinical pathways adapt?)
- Test ED operations without bed management system (manual tracking)
- Model discharge coordination without digital communication tools
This would reveal:
- Which clinical operations cannot safely continue without IT
- Where operational workarounds are unsafe or inefficient
- What recovery time objectives are actually required by patient safety
- Who makes clinical decisions during degraded IT capability
Re:State emphasizes that change management is essential but "rarely prioritised in hospitals." Operational resilience testing requires change management capability to design scenarios, coordinate exercises, implement lessons learned. Without expanding change management capacity, trusts can't do this effectively.
4. Account for operational debt in performance targets
The Medium Term Planning Framework locks trusts into 2% productivity improvement annually and ambitious operational targets.
But doesn't account for operational debt following major incidents. A trust experiencing significant cyber incident or operational crisis (equivalent to Synnovis impact) faces:
- Backlog of cancelled elective procedures
- Discharge delays cascading into bed availability
- Diagnostic pathway disruption creating downstream waits
- Staff exhaustion from working through crisis
This operational debt takes months to clear, even after underlying issue resolved.
The Framework should include provision for "operational resilience adjustment" – temporary target relief for trusts experiencing major disruption, conditional on:
- Incident properly reported and analyzed
- Operational resilience lessons implemented
- Recovery plan submitted and tracked
- Accountability for prevention of recurrence
Without this, trusts face perverse incentive to underreport or minimize incidents to avoid target failure.
Re:State's synthesis notes that reform will likely "slow the acceleration of costs, rather than cut them." Same principle applies to performance targets during recovery: focus should be on returning to trajectory, not maintaining impossible targets during crisis.
5. Map patient flow dependencies across organizational boundaries
Synnovis demonstrated that patient flow dependencies extend beyond individual trusts. Six trusts across south-east London depended on a single pathology provider. When it failed, regional flow collapsed.
NHS needs system-wide mapping:
- Which shared services are critical to patient flow? (Pathology, radiology, pharmacy)
- What's the concentration risk? (How many trusts depend on single provider?)
- What's the operational redundancy? (Can they failover to alternative provider?)
- What's the recovery time before patient safety compromised?
This should be maintained centrally by NHS England and updated as part of Integrated Care System planning. Currently nobody owns this visibility.
The Cyber Action Plan requires DHSC as Lead Government Department to have oversight of sector-wide cyber security. But doesn't require operational flow visibility across organizational boundaries.
You cannot manage sector-wide resilience without understanding sector-wide dependencies.
Re:State's synthesis emphasizes that hospitals operate as "complex web of relatively autonomous institutions." This makes cross-organizational mapping harder but more essential. Synnovis showed that autonomy doesn't prevent interdependence – it just obscures it.

The Uncomfortable Truth About Compounding Vulnerabilities
The reason government hasn't connected cyber resilience to operational resilience is that doing so would reveal how vulnerable patient care already is.
Re:State's analysis shows patient flow is critically degraded in steady-state operations:
- 13,740 patients stuck in hospital
- 268 excess deaths per week from A&E delays
- £1.7 billion annual cost from discharge delays
- 90% of nurses reporting patient safety compromised
Now overlay the Cyber Action Plan's assessment:
- 28% of infrastructure legacy and highly vulnerable
- Cyber risk "critically high"
- 2030 resilience target abandoned as unachievable
The system is operationally fragile during normal operations and running on infrastructure that's critically vulnerable to cyber attack.
This is not a hypothetical risk. Synnovis demonstrated that operational fragility and cyber vulnerability compound each other. The attack didn't just cause IT disruption. It caused operational collapse precisely because the underlying patient flow was already stressed.
If NHS patient flow was resilient – with operational redundancy, seven-day discharge workforce, real-time tracking tools, sufficient bed capacity – a cyber incident would be disruptive but manageable.
If NHS infrastructure was secure – patched systems, modern cyber controls, no legacy Windows 7 – cyber attacks would be less likely to succeed.
But NHS has neither operational resilience nor cyber resilience. Each amplifies the other's failure.
As discussed in the infrastructure piece, Re:State makes clear that technology only helps when the entire system is reformed alongside it. You can't fix patient flow with digital tools alone. You need:
- Financial incentives that reward efficiency rather than just activity
- Care pathways redesigned for modern clinical realities
- Workforce structures adapted to new ways of working
- Management capacity to implement and sustain change
- Infrastructure that can actually run modern tools
The Medium Term Planning Framework mandates digital transformation without addressing the infrastructure vulnerability the Cyber Action Plan identifies, the system reforms Re:State says are essential, or the management capacity needed to implement any of it.
Nobody has connected the dots: You cannot fix patient flow without digital tools. You cannot deploy digital tools on critically vulnerable infrastructure. You cannot secure infrastructure without investment. You cannot get investment without reformed capital approval. You cannot implement any of this without management capacity. You cannot deliver productivity targets without fixed patient flow. You cannot fix patient flow without system reforms beyond just technology.
It's a circular failure, and every document published in the last three months acknowledges one piece of the circle without acknowledging the whole.
The Next Synnovis (Coming to a Trust Near You)
When the next Synnovis happens – and the Cyber Action Plan makes clear it's a matter of when, not if – will NHS trusts be operationally resilient enough to maintain patient safety during IT disruption?
The answer, based on current trajectory, is no.
Patient flow is already critically degraded. Infrastructure is critically vulnerable. Digital transformation is mandated without infrastructure investment. Operational resilience and cyber resilience are planned in silos. Management capacity is insufficient to connect them.
The next cyber incident will be analyzed as a cyber security failure. It should be analyzed as a health system design failure – where cyber vulnerability and operational fragility were allowed to compound each other until patient harm became inevitable.
That's the conversation government is avoiding. These documents – published within three months of each other – reveal the problem in pieces. But nobody's willing to state the obvious conclusion:
The NHS cannot deliver the digital transformation mandated in the Medium Term Planning Framework on the critically vulnerable infrastructure identified in the Cyber Action Plan while patient flow remains as degraded as Re:State documents, without the management capacity Re:State says is essential, or the system reforms (financial incentives, care pathways, workforce structures) that Re:State identifies as prerequisites for technology to work.
Something has to give. Either:
- The timelines extend to match the Cyber Action Plan's realistic 2029+ completion
- The infrastructure investment materializes with ring-fenced NHS allocation
- The system reforms happen (financial models, care pathways, workforce training, management expansion)
- The mandates become performance targets that trusts predictably fail to meet
What we have now is strategic incoherence wrapped in policy documents that acknowledge different parts of the same crisis without admitting they're connected.
Synnovis was the warning. The question is whether government learns the actual lesson – that cyber risk and patient risk are the same thing, that operational resilience and cyber resilience cannot be planned separately, that technology without system reform creates digital dependency without digital resilience – or keeps treating them as separate problems requiring separate solutions.
Based on the last three months of policy documents, they're choosing the latter. And the next major cyber incident will prove that choice was wrong.

This fortnight I have been mostly eating mince pies and cream without any heed to the time of day. It's been a delight.
As a palate cleanser for all the Christmas music I've been forced to endure, I've been listening to this Bowie compilation by Adam Buxton.
Next issue I'll have gathered my wits enough to write about the ChatGPT foray into medical AI. Theres a lot of hot takes kicking about so I need to take my time to poke about before proclaiming that the sky is falling. It's consequential no doubt but I don't know how.
I'll sign off wishing you a cosy weekend and I hope we speak soon.
Take care x